Yesterday I was triggered by a colleague of mine that administrators of services in Azure or Office 365 are automatically required to login via Multi-Factor Authentication (MFA) when accessing the service in the future. When logging in to one of my tenants indeed a new conditional access policy listed in the conditional access blade of the Azure portal.
A new mandatory Baseline Conditional Access policy is created by Microsoft in every tenant;

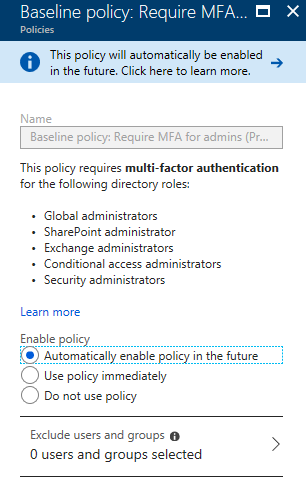
I think the reason for Microsoft of doing this is that still a lot of companies have high privilege accounts in their tenant without any MFA, at least I still see lots of companies not using MFA. Some for a reason, like Service Accounts but a lot of them because not seeing the threats of having high privilege accounts, like Global administrators, SharePoint administrator, Exchange administrators, Conditional access administrators and Security administrators, without MFA.
As a Global Admin you have the option to;
- Automatically enable policy in the future
- Use policy immediately
- Do not use policy
I would only not use this policy if you already have a process in place and you know for sure that all administrative accounts require MFA to access the tenant otherwise enable MFA on your privileged accounts and enable the baseline Conditional Access rule.
Currently this feature is in preview, as soon as the feature is general available the policy will be automatically enabled when you have the “Automatically enable policy in the future” option enable.
If you have privileged accounts (service accounts) that are used in scripts, you should replace them with Managed Service Identity or service principals with certificates. As a workaround, you can still exclude specific user (service) accounts from the baseline policy.
Read more here and be sure to take action!!!