 After the last blog about conditional access of Outlook Web App and SharePoint Online is forcing that the Managed Browser is used when accessing the service. This last part can be done via Active Directory Federation Service (AD FS). With AD FS you are able to allow or block access based on attributes of the client that is trying to authenticate.
After the last blog about conditional access of Outlook Web App and SharePoint Online is forcing that the Managed Browser is used when accessing the service. This last part can be done via Active Directory Federation Service (AD FS). With AD FS you are able to allow or block access based on attributes of the client that is trying to authenticate.
As part of the March update of the Managed Browser the Managed Browser is identifiable as ManagedBrowser via the UserAgent, before March the Managed Browser had a generic UserAgent.
So to be able to control access based on which browser is used a claim rule needs to be added that only allows traffic from the Managed Browser. The following claim rule will allow Managed Browser access, together with your other claim rules that control access to Office 365. (see for some options here)
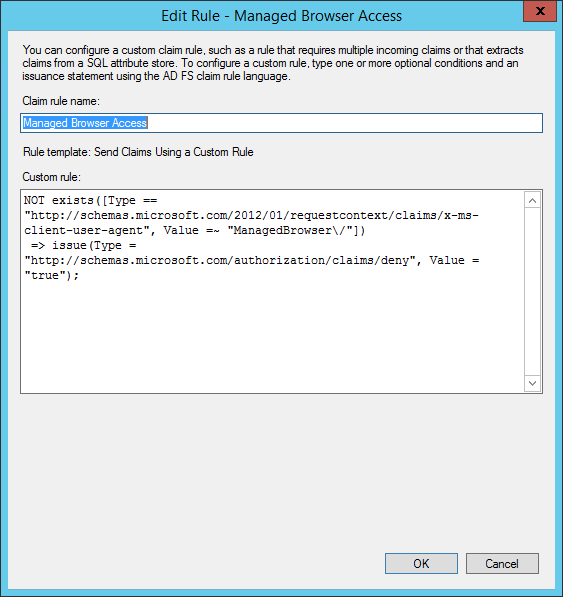
Add the following claim rule to the Insurance Authorization Rules of the Microsoft Office 365 Identity Platform relying trust partner:
NOT exists([Type == “http://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-client-user-agent”, Value =~ “ManagedBrowser\/”])
=> issue(Type = “http://schemas.microsoft.com/authorization/claims/deny”, Value = “true”);
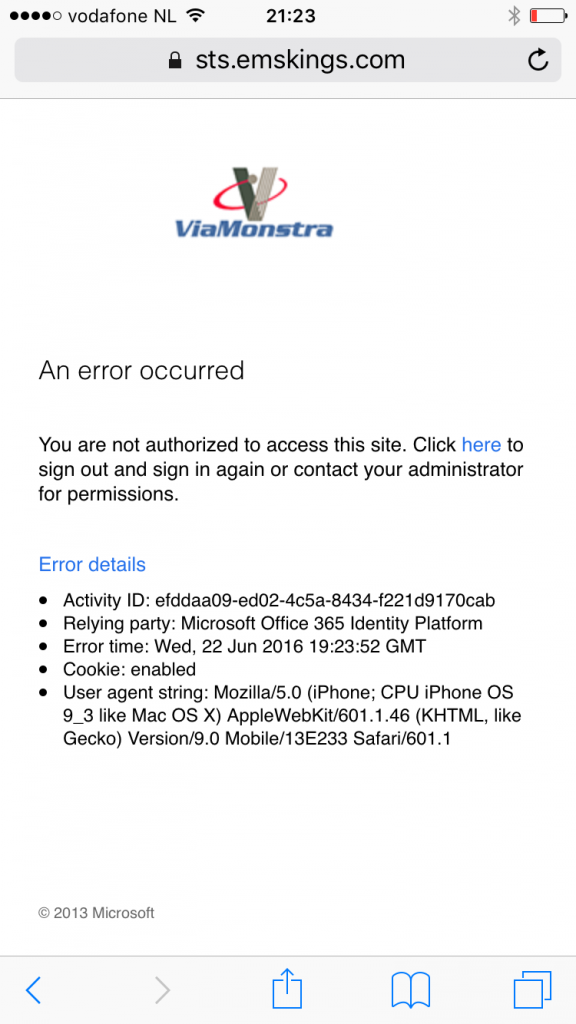
After adding this claim rule access to OWA or SharePoint Online via the normal browser is blocked by default, accessing the service via the Managed Browser is allowed.
 |
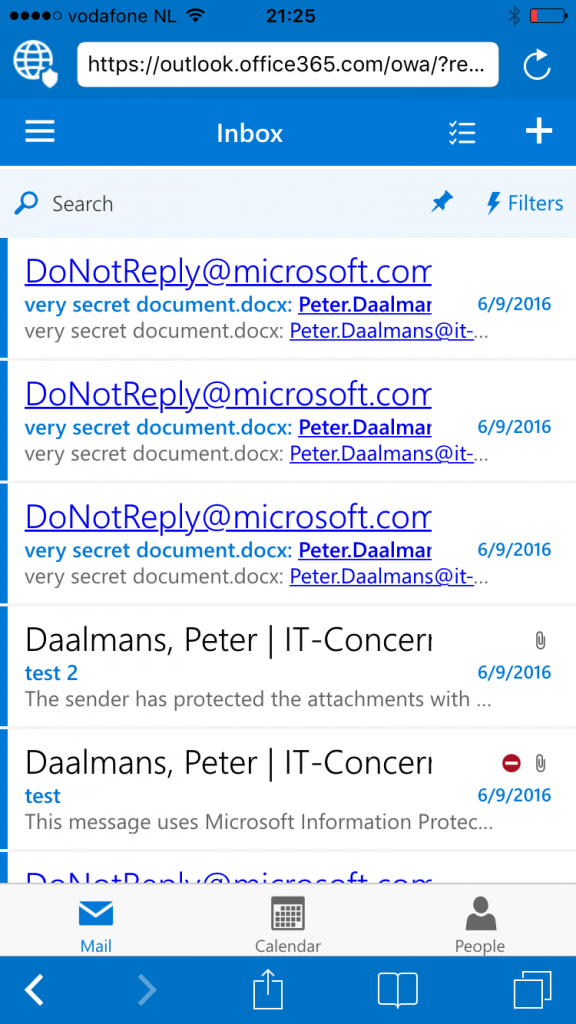 |
Note in this example only the claim rule for the Managed Browser is used..
Off course there are ways to maybe spoof the User Agent of a Browser, but to be able to bypass spoofing we can enable device authentication on AD FS. With this setting we are able to check if a device is managed or not. Definitely a subject for another blog for the near future.



The “ManagedBrowser” string is only sent from IOS devices. It does not work on Android.
Do you know of an equivalent way of doing this with Azure AD / Azure AD App Proxy?