
Mobile devices with Android are very popular but still a pain to really manage them in a descent way and keeping the device and the data on it secure. With the new version Android 6 (Marshmallow) which is currently rolled out, Google is securing the devices by default with device encryption. Which is a good thing if you ask me.
If you still have an Android device of an earlier version, you may also want to encrypt the device. A couple of tips if you are using Intune to manage Androids or if you are thinking of using Intune and starting to secure your devices.
If you want to encrypt your device, Android forces you to configure an encryption key which exist of 6 characters with at least one number. This is done to be able to make the device better protected against brute force attacks. If you are going to force complex passwords instead of passcodes than this is a good thing, but if you are using passcodes this can be confusing for your users since the user needs to enter the encryption key after a reboot of the device. (iOS and Windows devices are encrypted by default but the encryption key is safely stored in the device its hardware)
Using an MDM solution like Microsoft Intune you are able to configure passcode/password configuration policies. Setting a different configuration policy for instance for to use a 6-digit passcode after a user has encrypted their device will force the user to reset their passcode again.
[table style=”1″] [tr][td]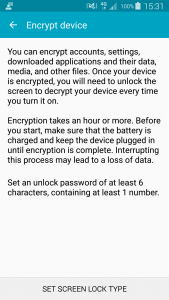
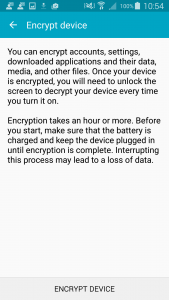
To make it more convenient for the user enable encryption while enrolling into Microsoft Intune, this way a user only needs to change their passcode/password once.
- Configure passcode/password policy
- Configure encryption as part of configuration policy
- Enforce passcode/password policy and encryption via compliance policies to block access to corporate data
access to company data is not allowed until the device is compliant.
The stronger the passcode/password policy the stronger the protection via encryption. For instance, a 4-digit code is found easier via a brute force attack then a 6-digit code, but a 6-digit code is found much easier than a 6-character password. The more complex the encryption key is the better the encryption. It is all about usability versus security. Identify what kind of classified data the users are able to access via the device and what apps are being used. For instance if you are using the MAM enabled Office apps to access mail and documents, then the data of the app is also encrypted by the app. So this may allow you to use a less strong passcode/password on device level then when using the native mail app of Android.
Be sure to stay in close contact with your security department.


